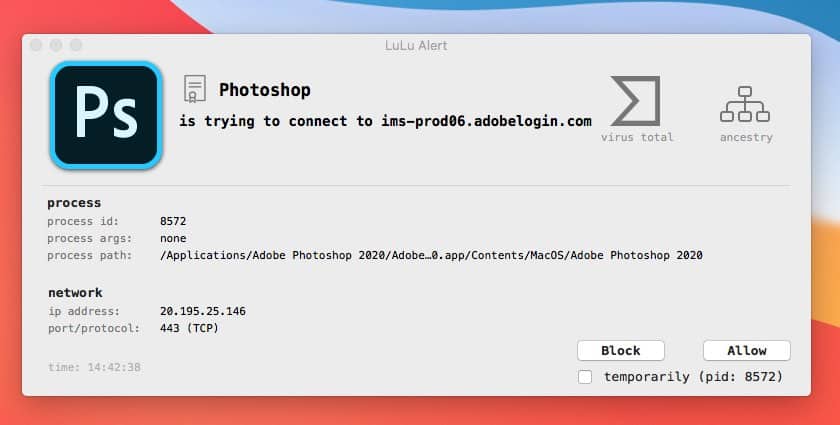
You can use either Windows firewall to block all outbound link from Adobe, or you may also use Windows host file to block those URL. Today I am not going to share how to block any software outbound link using Firewall, because I dont want to write a very long article. Once installed, Little Snitch monitors your internet traffic and every time it detects an outbound connection, for example, Adobe Reader trying to access the internet, it pops up a window and ask you if you want to allow the connection one time, or make a rule to allow. Block outgoing connections (Little Snitch, Hands Off! Switch the outbound connections setting from Allow (default) to Block on all profile tabs. Additionally, click on the customize button on each tab next to Logging, and enable logging for successful connections. The changes block all outbound connections of processes unless a rule exist that allows the process to make outbound connections. After that, click on ‘Next’ again. Now select the option that says ‘ Block the connection ’, which should be marked by default. Then click on ‘Next’. Now, choose all Domain, Private and Public, to stop Internet access for Adobe Photoshop for all types of networks, and click on ‘Next’. Block all outgoing connections of Adobe using the Lulu software (use search option for “adobe”) I count 23 connections in the rules section of Lulu!Now it gets weird; use latest version of Zii (5.1.9) Adobe Photoshop and Illustrator are both showing the “K’ed by TNT Team” at the Help menu. However Lightroom doesn’t seem to work.
OS X v10.5.1 and later include an application firewall you can use to control connections on a per-application basis (rather than a per-port basis). This makes it easier to gain the benefits of firewall protection, and helps prevent undesirable apps from taking control of network ports open for legitimate apps.
Configuring the application firewall in OS X v10.6 and later
Use these steps to enable the application firewall:
- Choose System Preferences from the Apple menu.
- Click Security or Security & Privacy.
- Click the Firewall tab.
- Unlock the pane by clicking the lock in the lower-left corner and enter the administrator username and password.
- Click 'Turn On Firewall' or 'Start' to enable the firewall.
- Click Advanced to customize the firewall configuration.
Configuring the Application Firewall in Mac OS X v10.5
Make sure you have updated to Mac OS X v10.5.1 or later. Then, use these steps to enable the application firewall:
- Choose System Preferences from the Apple menu.
- Click Security.
- Click the Firewall tab.
- Choose what mode you would like the firewall to use.
Advanced settings
Block all incoming connections
Selecting the option to 'Block all incoming connections' prevents all sharing services, such as File Sharing and Screen Sharing from receiving incoming connections. The system services that are still allowed to receive incoming connections are:
- configd, which implements DHCP and other network configuration services
- mDNSResponder, which implements Bonjour
- racoon, which implements IPSec

To use sharing services, make sure 'Block all incoming connections' is deselected.
Allowing specific applications
To allow a specific app to receive incoming connections, add it using Firewall Options:
- Open System Preferences.
- Click the Security or Security & Privacy icon.
- Select the Firewall tab.
- Click the lock icon in the preference pane, then enter an administrator name and password.
- Click the Firewall Options button
- Click the Add Application (+) button.
- Select the app you want to allow incoming connection privileges for.
- Click Add.
- Click OK.
You can also remove any apps listed here that you no longer want to allow by clicking the Remove App (-) button.
Automatically allow signed software to receive incoming connections
Applications that are signed by a valid certificate authority are automatically added to the list of allowed apps, rather than prompting the user to authorize them. Apps included in OS X are signed by Apple and are allowed to receive incoming connections when this setting is enabled. For example, since iTunes is already signed by Apple, it is automatically allowed to receive incoming connections through the firewall.
If you run an unsigned app that is not listed in the firewall list, a dialog appears with options to Allow or Deny connections for the app. If you choose Allow, OS X signs the application and automatically adds it to the firewall list. If you choose Deny, OS X adds it to the list but denies incoming connections intended for this app.
If you want to deny a digitally signed application, you should first add it to the list and then explicitly deny it.
Some apps check their own integrity when they are opened without using code signing. If the firewall recognizes such an app it doesn't sign it. Instead, it the 'Allow or Deny' dialog appears every time the app is opened. This can be avoided by upgrading to a version of the app that is signed by its developer.
Enable stealth mode
Enabling stealth mode prevents the computer from responding to probing requests. The computer still answers incoming requests for authorized apps. Unexpected requests, such as ICMP (ping) are ignored.
Firewall limitations
The application firewall is designed to work with Internet protocols most commonly used by applications – TCP and UDP. Firewall settings do not affect AppleTalk connections. The firewall may be set to block incoming ICMP 'pings' by enabling Stealth Mode in Advanced Settings. Earlier ipfw technology is still accessible from the command line (in Terminal) and the application firewall does not overrule any rules set using ipfw. If ipfw blocks an incoming packet, the application firewall does not process it.
Block Outgoing Connections For Adobe Products Free
Security setup
Block Outgoing Connections For Adobe Products Windows
PeerBlock makes your online activities much safer by taking control of who your PC talks to on the Internet. Developed by the PeerBlock Project, it is the most advanced IP blocking utility which gives you the ultimate power to block the sleazy spyware companies, unethical advertisers, and certain cyber entities you don't want to look at your PC's operations. This open-source freeware has been around since 2003 with its predecessor PeerGuardian giving its users a reliable and guaranteed protection from unwanted online attention. But will this software still shine within the array of modern VPN services? There's only one way to find out. Learn more here.
The most popular IP blocking utility
Overall, PeerBlock may be the best online security software for the past years but its current protection is now incomparable with any modern VPN services have to offer.
The software allows you to control how your PC interacts with other computers online. It will scan your computer for in- and outgoing connections to different IP addresses which are deemed malicious or unwanted. While other forms of online security programs such as firewalls will let you block hosts one by one, the software will make it easier for you to block all the malicious online addresses at once by providing frequently-updated lists of host addresses. These lists are further divided into various distinct categories including spyware, advertising, education, and peer-to-peer. The spyware list is the most common problem that can be solved through the software. By using the app to block malicious sites, you can now surf the Internet with peace of mind. Interestingly, the education list is popular for the younger generation. This list is primarily blocked by students who are probably uncomfortable about the fact that their colleges monitor their online activities. While the P2P list is a collection of media companies who are bound by confidentiality and copyright laws and often blocked by the people who like to do the grievous act of online piracy. And lastly, the software’s ability to block the advertising list is probably the most helpful of all. By adding this list to your blocklist, you may now enjoy advertisement-free browsing on your favorite social media and online sites.
If you’re a first time user, a wizard box will pop up to display set-up options on the software’s first run (though you can change them anytime you want). Aside from adding a list of IP addresses to your blocklist, there’s also a checkbox labeled Always Allow HTTP for you to explore. This option will always enable connections over ports 80 and 443 of your PC (which are often used for browsing the Internet) even if they’re included on your blocklist. After completing the software’s easy-to-finish setup, you can now tick the software’s update schedule and other options. To proceed, just click the Finish button. Immediately after, the software will quickly download an updated list of known threats that can be troublesome to your PC in a simple (but intuitive) interface which is composed of two self-explanatory tabs namely, Protection and Settings (which is a two-page stretch). To open the software’s main console, you just have to right-click the system tray icon. While doing a left-click will lead you to the context menu for easier and instant access to Enable and Disable controls, allow HTTP options, basic controls at the top side, and Support.
By using the software, you’ll be protected from certain cyber bodies that can cause harm and trouble with your PC and personal life online. Although, even the software’s creators are seriously warning the users to be careful and vigilant in their daily online activities. You should not depend on the software too much, and if possible, avoid entering malicious websites at all since trackers can easily change their IP addresses in an instant without the software knowing.
Where can you run this program?
The software is currently available for Windows users exclusively. With the software’s slow release of updates, it is hard to say whether the creators are planning to expand its reach to Mac OS, as well as to Android and iOS mobile phones. You can download the software for free by visiting its developer’s official website. Since its release, it still has a minimal user base with only over 690,000 number of downloads up-to-date.
Is there a better alternative?
Since the software doesn’t have the ability to hide your IP address, it will not necessarily make you anonymous online. You can simply block a wide range of IP addresses from giving you unwanted disturbance but they can still be able to see and track your activities online (legal or not). For better and secure browsing, it is recommended for you to use a VPN service such as Private Internet Access and IPVanish. PIA is the most popular choice of VPN users because of its extreme low subscription fee.
Our take
Definitely, the software is more than a firewall program that protects your online identity. It is a useful first-line defense against inappropriate sharing of your sensitive and confidential information to anyone online. While the software offers a lot of helpful features, getting the most out of it may require a little bit of technical savviness. Depending on how your computer connects to the Internet and the settings of your firewall and ISP, you may be required to tweak some things to ensure that its services are still in-line with your cybersecurity needs. On the other hand, it has a neat and easy-to-understand interface with an online well-updated public forum. You can add new particular items to your blocklists, or unblock a particular array of IPs with ease.
Should you download it?
Only if you're up for a simple (but reliable) first line of online security. The software is only worth trying if you're curious to see how many sites and online entities are trying to reach your computer during your average browsing session. Although, if you're really looking for better cybersecurity with a better scope other than IP blocking capabilities, then try looking for the best VPNs available for purchase.
Highs
- Free download available
- Simple but intuitive interface
- Well-updated public forum
Lows
- Impossible to block all malicious IPs
- Can block even good peers causing slower connections
PeerBlockfor Windows
Block Outgoing Connections For Adobe Products Online
1.2